
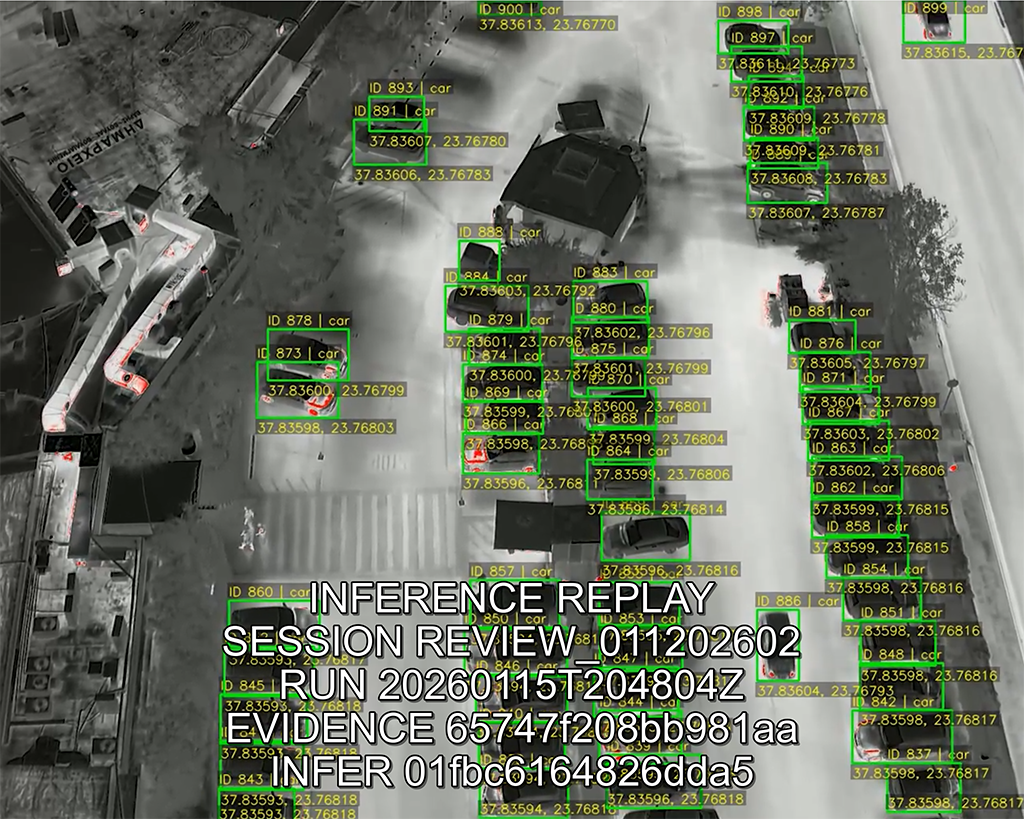
Enter your evaluation code to mint time-limited download links.
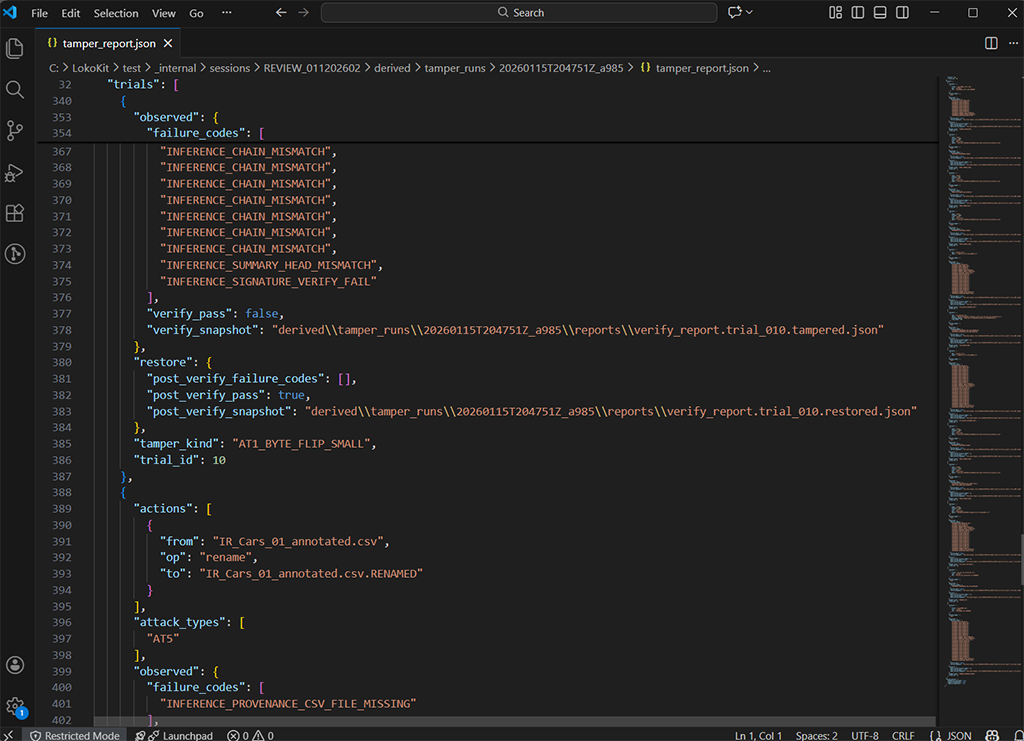
.\lokokit.exe run --loko C:\LokoKit\incoming\011202602_dist.loko --out-session REVIEW_011202602 --forcePROOF_FFMPEG="$PWD/third_party/ffmpeg/ffmpeg" ./lokokit run --loko ~/LokoKit/incoming/011202602_dist.loko --out-session REVIEW_011202602 --forcechmod +x ./lokokit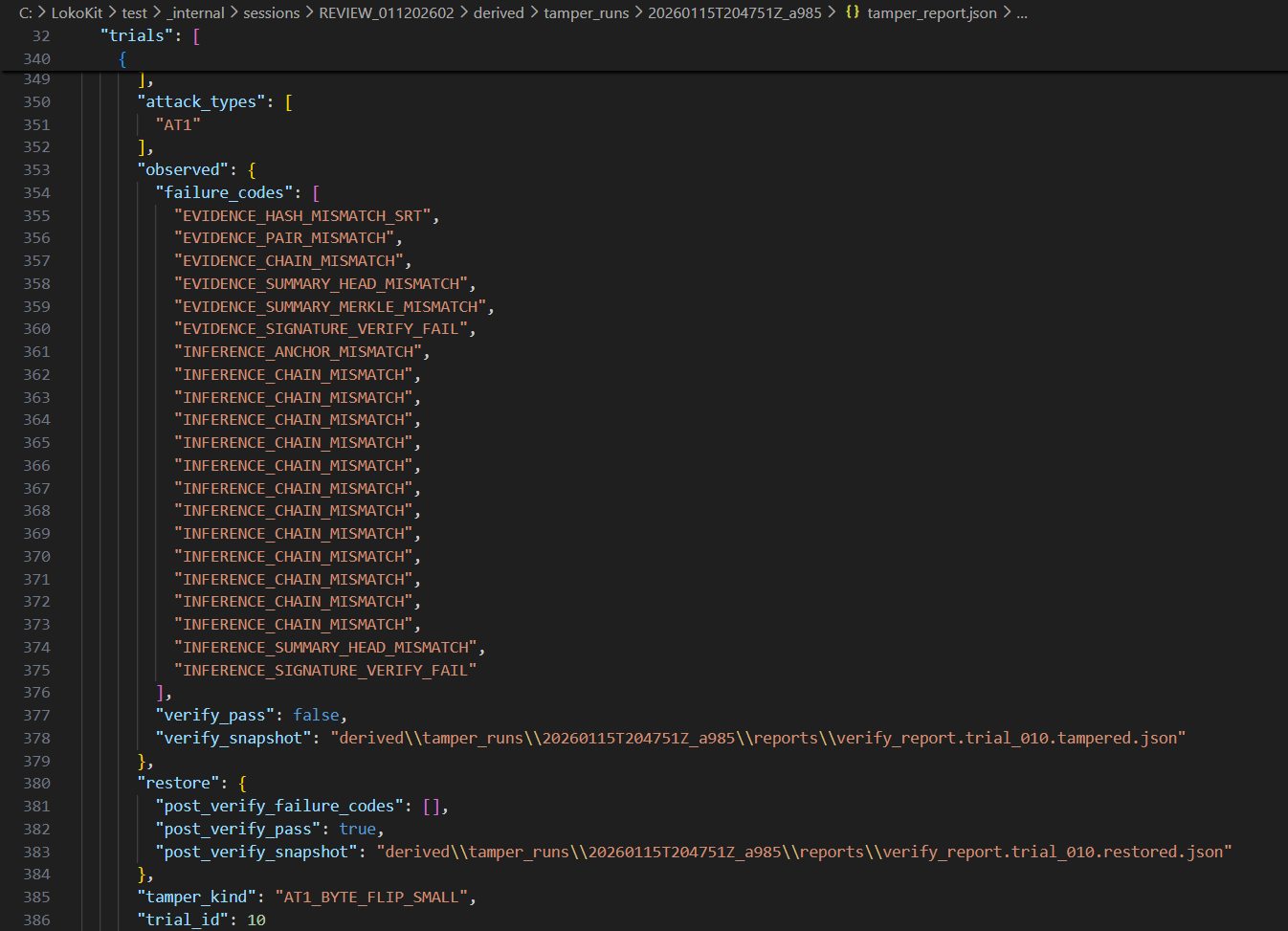
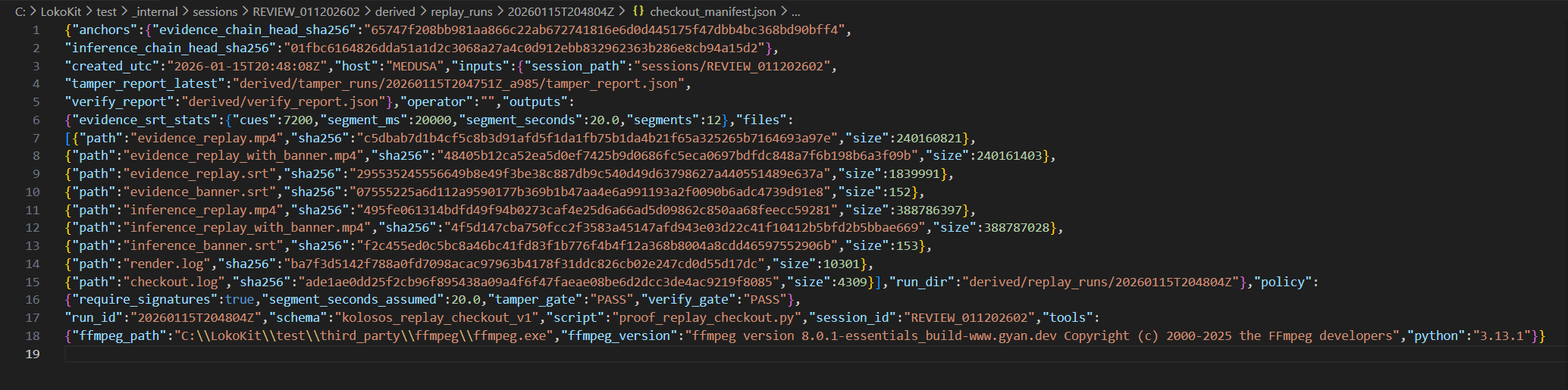
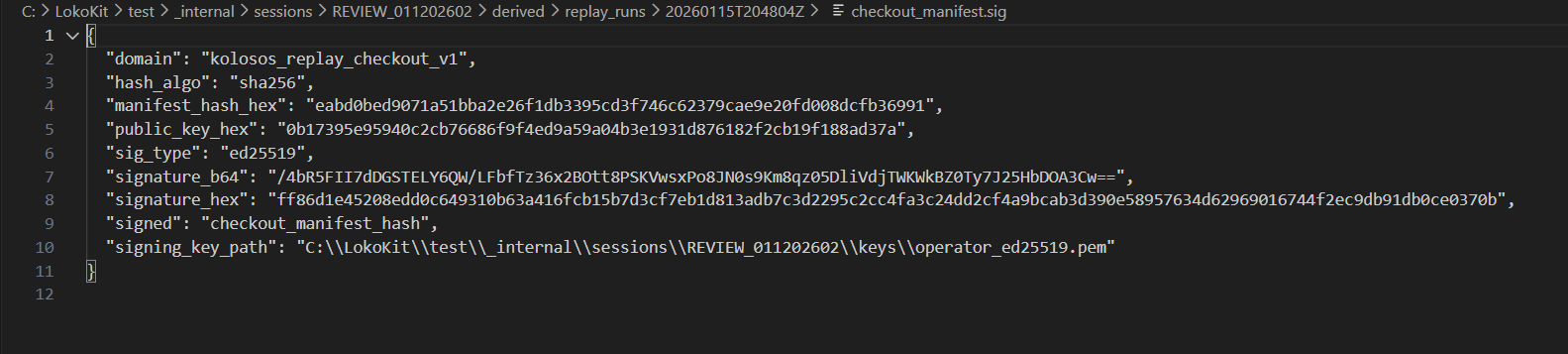
.loko Evidence Package is structurally valid and internally consistent..loko packages or customer data.